Phishing emails are among the most common tools used by cybercriminals to steal personal information, spread malware, or trick victims into fraudulent activities. These emails often masquerade as legitimate communications, preying on the unsuspecting. Recently, LinkGuard analyzed a suspicious email to reveal how such scams operate and the key red flags that can help individuals stay safe.
The Suspicious Email
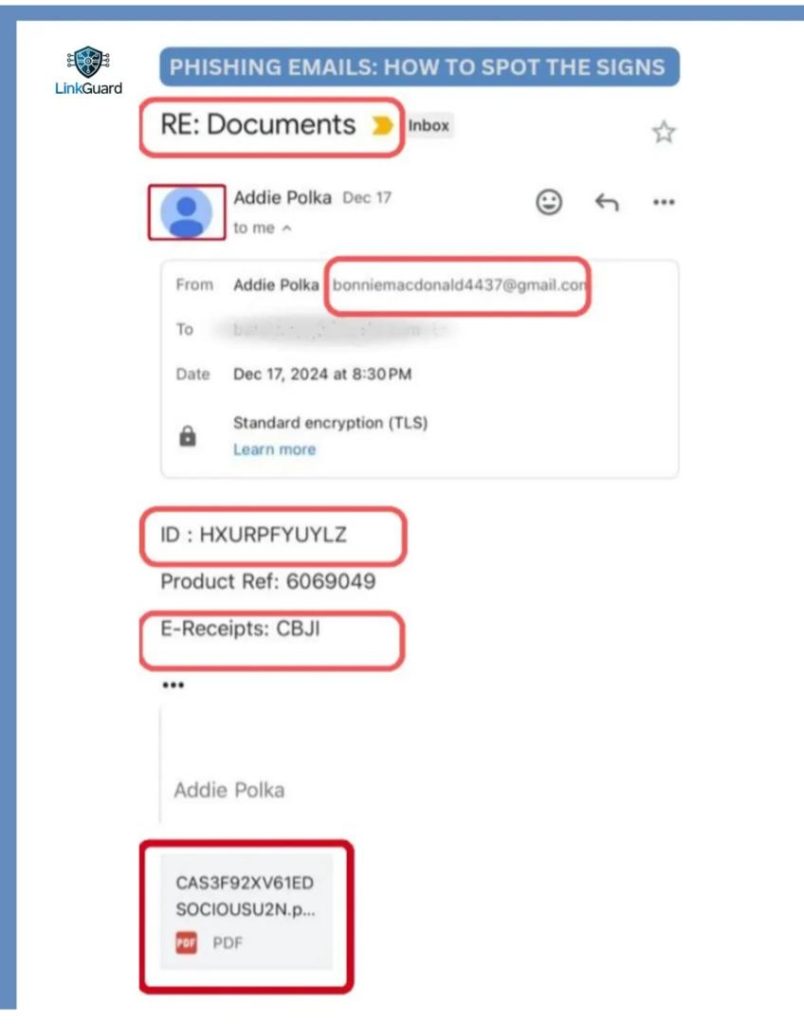
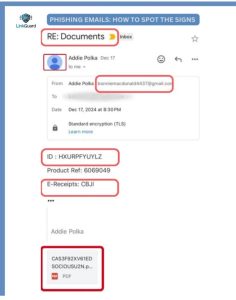
On December 17, 2024, an email with the subject line “RE: Documents” landed in a recipient’s inbox. At first glance, it appeared like an important follow-up message, but a closer inspection revealed its malicious intent. Here’s a breakdown of the deceptive tactics used:

1. Suspicious Sender Email Address
The email was sent from bonniemacdonald4437@gmail.com, a randomly generated address. Legitimate businesses rarely use generic email services like Gmail for official correspondence.
Fact-Check: Businesses typically use branded email addresses that match their domain name (e.g., support@company.com). This mismatch is a clear sign of a phishing attempt.
2. Vague and Misleading Content
The subject line, “RE: Documents”, is generic, aiming to mislead the recipient into believing it’s a follow-up to a previous conversation. The body of the email included cryptic references to an ID (HXURPFYUYLZ), Product Ref (6069049), and E-Receipts (CBJI), with no explanation or context provided.
Fact-Check: Genuine emails typically offer clear and specific details about the purpose of the communication. The vagueness here is a tactic to provoke curiosity and lure the recipient into further engagement.
3. Malicious PDF Attachment
The email included an attached file named CAS3F92XV61EDSOCIOUSU2N.pdf, with an odd and auto-generated name. Such attachments in phishing emails often contain harmful links or scripts designed to steal data or infect devices.
Fact-Check: PDFs from unknown senders should always be treated with caution. Cybercriminals use seemingly innocuous files to deliver malware.
4. Lack of Branding or Official Details
The email lacked any company logos, official signatures, or professional formatting. Legitimate organizations include branding elements and contact details to ensure authenticity.
Fact-Check: The absence of branding is a hallmark of phishing emails, as scammers often avoid using copyrighted logos to reduce the risk of detection.
5. Urgency and Ambiguity
The random codes and unexplained references were coupled with an urgent tone. This is a common strategy to pressure recipients into acting quickly without verifying the email’s legitimacy.
Fact-Check: Legitimate companies provide clear, actionable instructions and do not rely on urgency to compel responses.
A Deceptive Follow-Up: Fake Invoice
The phishing email included a follow-up PDF resembling an invoice from McAfee, claiming a charge of $695.88 for an antivirus subscription. It urged the recipient to contact a phone number (+1 803-269-5028) if they didn’t authorize the transaction.
Fact-Check:
- Impersonation: Cybercriminals often impersonate well-known companies like McAfee to appear legitimate.
- Fake Contact Details: The provided phone number is not associated with McAfee. Scammers use these numbers to extract personal or financial information from victims.
- No Prior Communication: The recipient had no prior subscription with McAfee, making this unsolicited email suspicious.
LinkGuard’s Verdict
This email is a classic phishing attempt designed to trick recipients into opening a malicious attachment or contacting scammers. LinkGuard advises:
- Never open attachments or click on links from unknown senders.
- Verify the sender’s email address and the legitimacy of the content.
- Report suspicious emails to your email provider or cybersecurity tools.
Stay vigilant and safeguard your digital life.