This link, https://afatm.org/, has been circulating online, promising users easy rewards and points for completing simple tasks. At first glance, it may seem like a harmless online opportunity, but a deeper analysis reveals signs of a hacking scheme. Below is a step-by-step breakdown of the process, how scammers craft it to entrap users, and what makes it suspicious.
1. Homepage with Enticing Promises
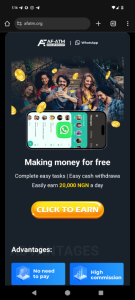
When you click the link, it directs you to the homepage. The homepage is designed to be flashy and persuasive, offering promises of quick rewards with you earning just by clicking a button
- What’s wrong: These promises are designed to lure users into a false sense of security, making them eager to proceed without asking questions. The urgency and appeal are intentional distractions.
- Why scammers act this way: Scammers understand that flashy promises are an effective way to exploit human emotions, particularly greed and impatience. This increases the chances of users continuing to the next steps.
2. Redirect to the Register and Login Page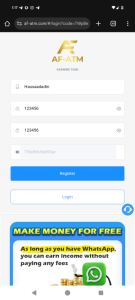
The next step is being prompted to register and login. Here, users are asked to register under the guise of creating an account.
- What’s wrong: Asking for sensitive details like names at this stage is suspicious. Legitimate platforms are upfront about how this data will be used, but this site lacks transparency.
- Why scammers act this way: Collecting personal information is a critical step for scammers and hackers. This data is valuable for identity theft, spam campaigns, or even resale to other fraudulent groups.
3. Inputting Your Phone Number
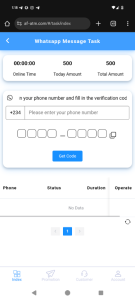
Next, you are asked to input your phone number. This step moves beyond registration into harvesting more personal details.
- What’s wrong: Legitimate platforms rarely ask for phone numbers unless there’s a clear purpose, such as two-factor authentication. In this case, the purpose is unclear, raising concerns.
- Why scammers act this way: Phone numbers are a gateway for hackers to gain access to more sensitive information. By obtaining your number, they can attempt to bypass two-factor authentication, intercept messages, or exploit vulnerabilities to hack into your accounts. Additionally, it provides a direct line for targeted phishing attacks or spreading malicious links.
4. Linking to WhatsApp

Users are then asked to link their WhatsApp accounts.
- What’s wrong: Linking WhatsApp is unnecessary for a legitimate platform to function. This request is often a tactic used by hackers to gain access to personal conversations, contacts, and shared media. By linking WhatsApp, hackers can infiltrate your network, spread malicious links, and potentially hijack your account to carry out further attacks.
- Why scammers act this way: Hackers exploit trust within social circles. By gaining access to your WhatsApp account or contact list, they can send malicious messages or links that appear to come from a trusted source. This makes the attack seem more credible and increases the likelihood of others falling victim, creating a chain reaction of compromised accounts.
5. Alleged Rewards for Staying Online
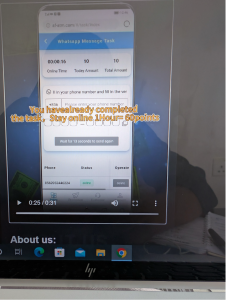
Finally, the site claims you will earn points or rewards for staying online and completing tasks.
- What’s wrong: These rewards are often fake, displayed merely to keep users engaged. No real benefits materialize, leaving users trapped in a cycle of hope and frustration.
- Why scammers act this way: The illusion of rewards keeps victims engaged, giving hackers more time to collect sensitive information, deploy malicious software, or gain deeper access to personal accounts and networks. This tactic ensures users remain distracted while their data and digital security are being compromised.
The Big Picture: How It All Fits Together
The entire process is meticulously designed to manipulate users. The homepage creates excitement, the registration builds trust, and each subsequent step lures users further into the scam. By the time users realize something is wrong, they’ve often shared enough personal information to put themselves at risk.
Conclusion
While the initial steps may seem harmless, the process reveals clear signs of a hacking scheme. Each step strategically exploits human emotions and trust, harvesting data and spreading the scam further. Always exercise caution when dealing with unfamiliar links, and remember: if something sounds too good to be true, it probably is.

